cone of silence
Diagram to discuss layers of information sharing
Using the perspective of threat emulation, I created the the Cone of Silence to discuss the obstacles I faced in my research for my 2019 GrrCon Presentation, Dance, Fancy Bear. Dance! This diagram attempts to explain the relationship between information collection and the amount of discernment needed when divulging information discovered publicly.
I meet a lot of researchers that feel information sharing is an obstacle. But really, it’s just a maze to navigate. Hopefully this diagram can help navigate that maze.
Cone of Silence for information dissemination
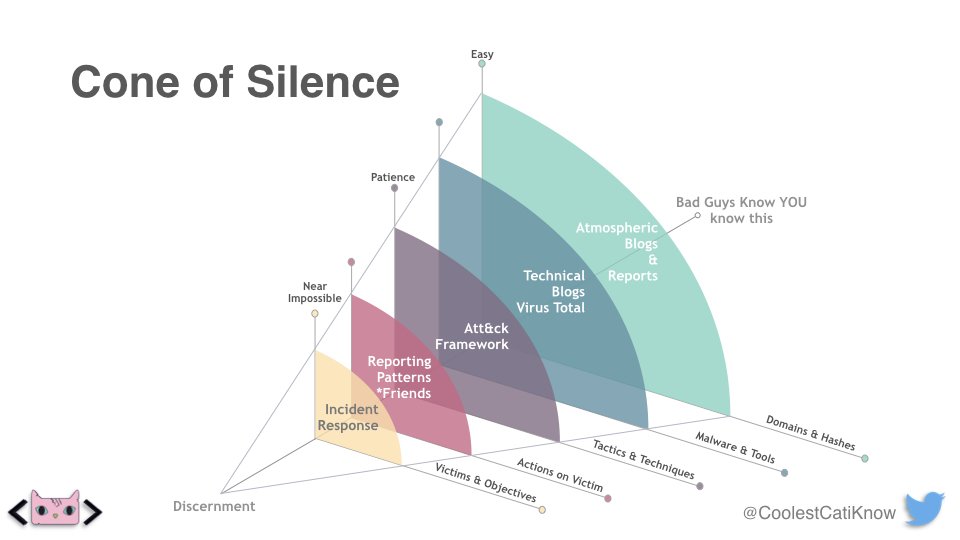
The Cone of Silence diagram is composed of five types of information (layers) along an axis of common sense regarding what happens if this information is discussed publicly (AKA discernment). The further down the cone you go, the harder the information is to collect due to the impact to the victim. Also, the further down the cone you go, the more consideration is needed in how information is treated (even casual offhand drunken remarks🍻).
The Layers
The best way to read the Cone of Silence is to start from the outside of the cone (domains & hashes) and move towards the center (victims & objectives).
Domains & hashes - Commonly referred to as indicators of compromise, these can include command and control domains, domains to host malware, and hashes of malicious executables used in the operation.
Malware & tools - Malicious executables, identified post-exploitation toolsets and macros documents.
Tactics & techniques - A threat actors historical behaviors and common methods used by others with similar motives.
Actions on victim - Behaviors in victim environments, how the environment was navigated, and methods of exploitation.
Victims & objectives - Name of the victim and the specific information the threat actor was searching to obtain.
The Cone of Silence might apply when...
Publishing a new detection. For example, let’s say you find a series of strings in a payload and then announce it to the world as a great way to detect the latest and greatest malware. You tweet it and get lots of ❤️. Only to get a DM from your companies security department stating that after your tweet, the adversary changed the string. Now they have to find something else to key off of for detection.
You are publishing an emulation plan on the world wide web. Here is a fictional scenario. You are writing an emulation plan and your buddy tells you some of actions a threat actor did in their environment before they kicked them out. Such as stealing VPN certificates and using a specific exploit for a VPN service provider. You then publish this behavior as apart of your emulation plan on Github and link it to Twitter. This get’s lots of Twitter ❤️s. And suddenly your buddy tells you the adversary you emulated changed tactics and was back in his environment. The adversary might have been one of your Twitter ❤️s.
Precautions look like…
Only discussing information in encrypted channels
Being upfront with what is needed for your project verses what’s cool
Asking if it’s okay to share information or use it before you actually do (and be honest with what you are using it for)
Discussing sensitive information with intention rather than casually (i.e. technical discussion on adversary intent verses gossip about the company)
A little background
Sometimes a person gets dropped into your life just to have a specific conversation with you that sparks a thought ✨ and plants a seed 🌱. That’s what sparked this blog post. What started as a casual lunch conversation turned into a serious conversation about human trafficking. My lunch partner (let's call them Smith) was expressing their frustration about an inside man in a criminal organization who was not sharing information about ongoing operations. Smith could not understand why someone would withhold information that could stop human trafficking operations. That's when the spark hit me ✨😲. Smith didn't understand the cost of that information. We are all familiar with the idea of the inside man on the drug organization. But there are additional costs to him getting discovered. Such as the way the organization communicates, schedules, logistics, methodology of operations. Basically when someone gets found out it causes a domino affect.
Over the next couple of weeks, I thought a lot about our conversation. As I was preparing for a threat emulation presentation, I was struck by the parallels between collecting open-source information on threat actors and my lunch conversation. I realized sharing information was not a problem to solve but rather a maze to navigate. Thus, the Cone of Silence was born.
So how do we make information more accessible without bringing harm to those bringing it to light?
No idea and not the point of this post. If it was an obvious solution we would have already fixed it. But we can reframe this from an obstacle that blocks to a maze to navigate.
💖 Thank you Smith, you know who you are 💖
This is a tricky topic to write about, I would 😻 feedback on how to communicate these ideas better.